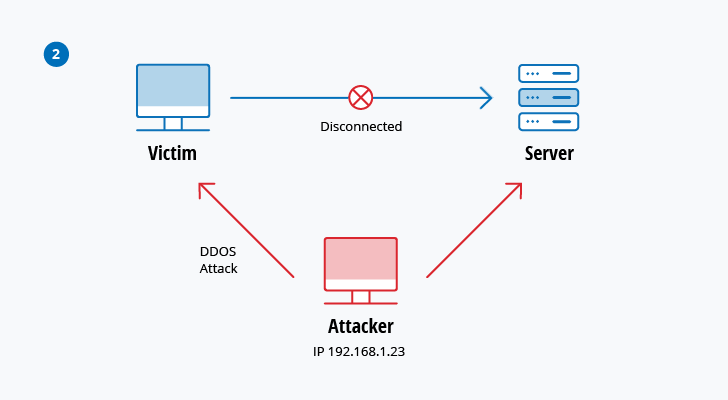
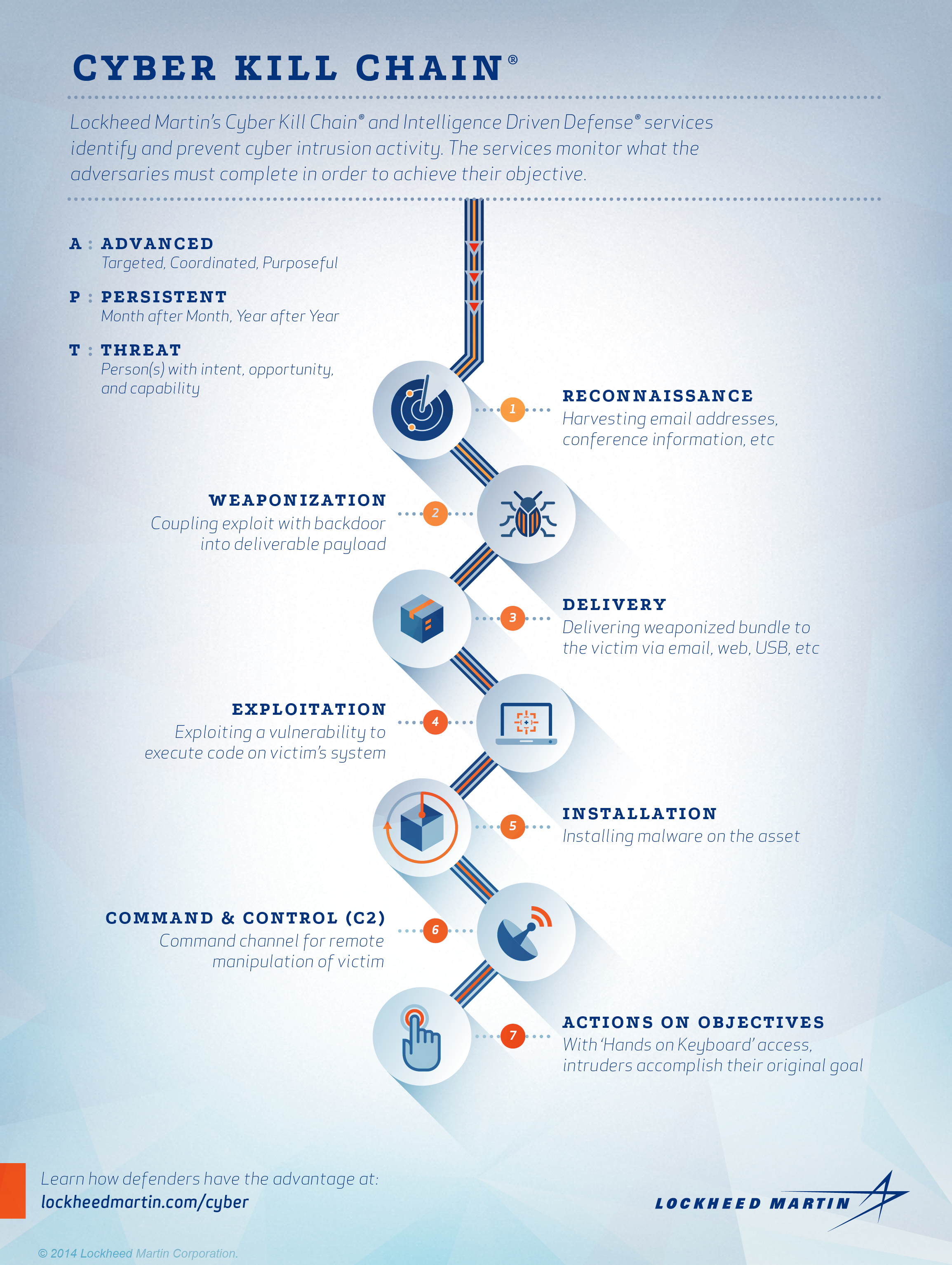
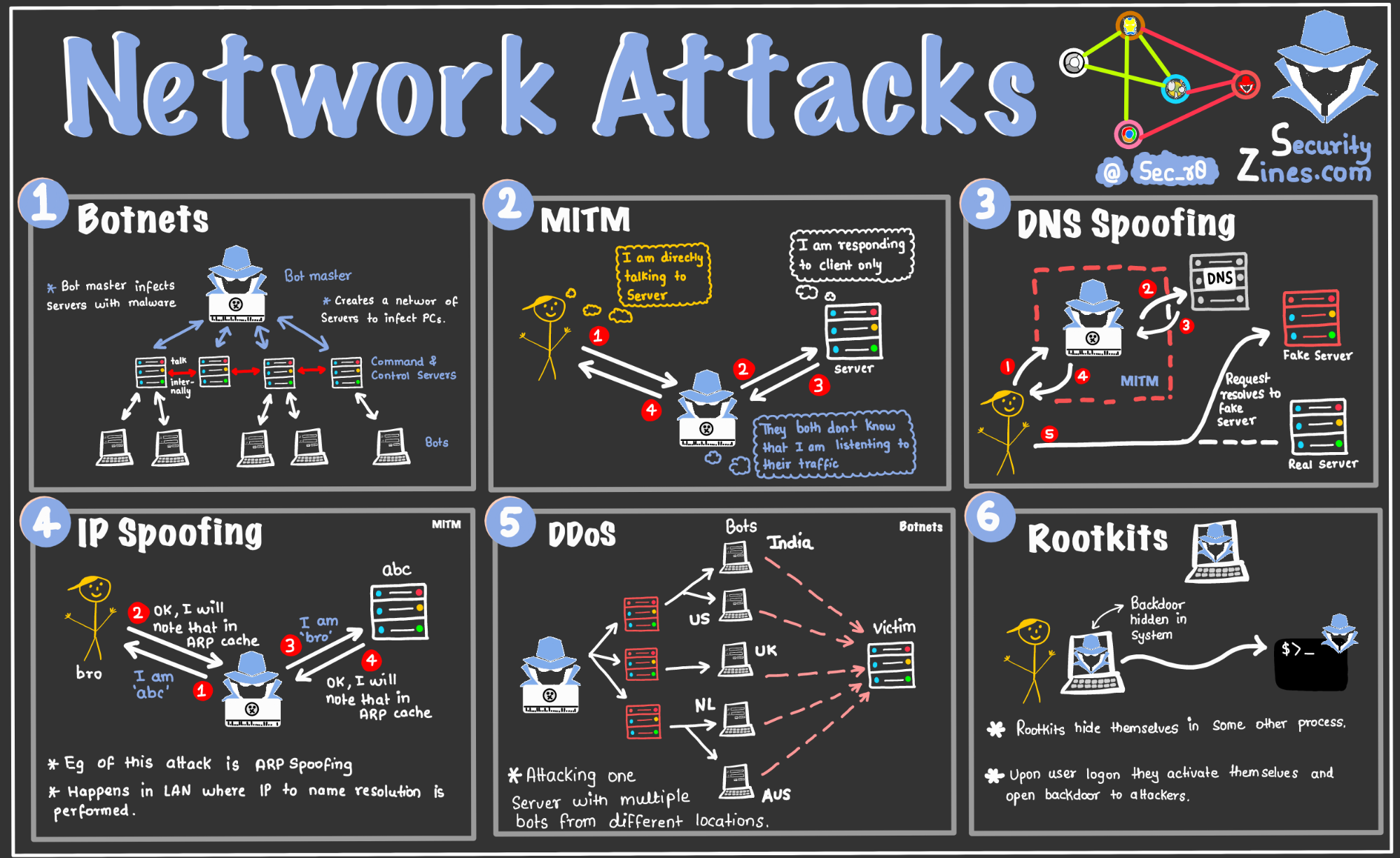
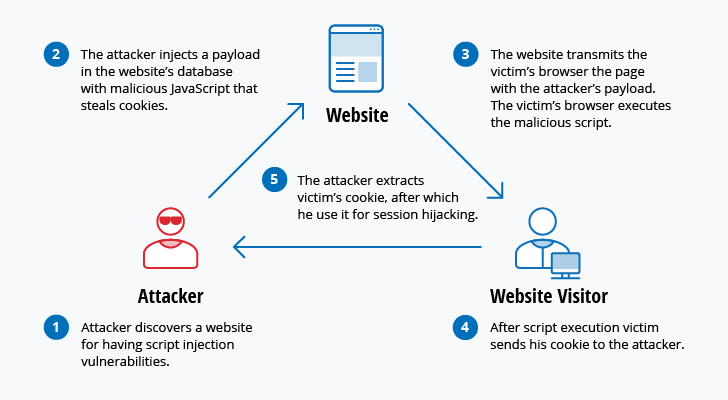
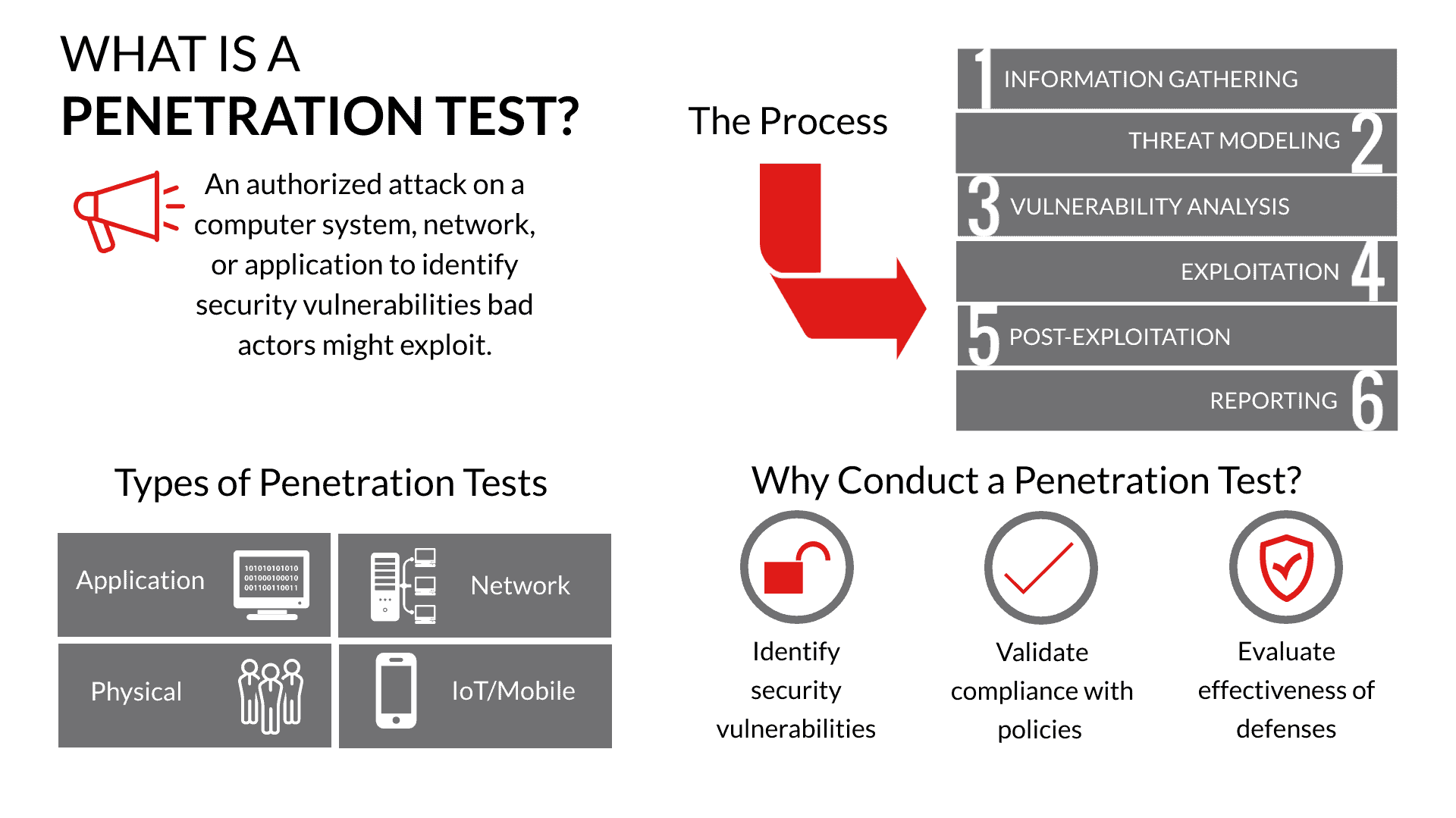
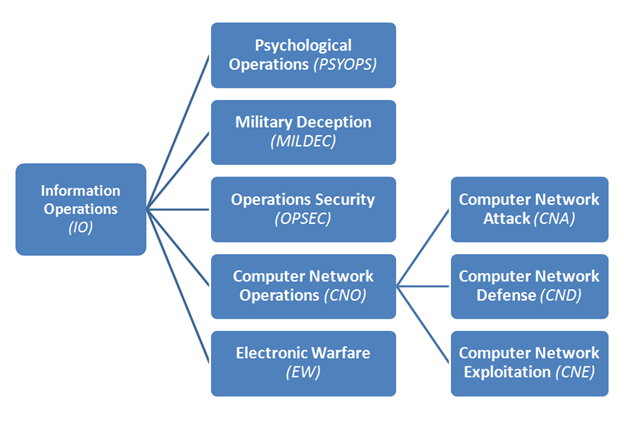
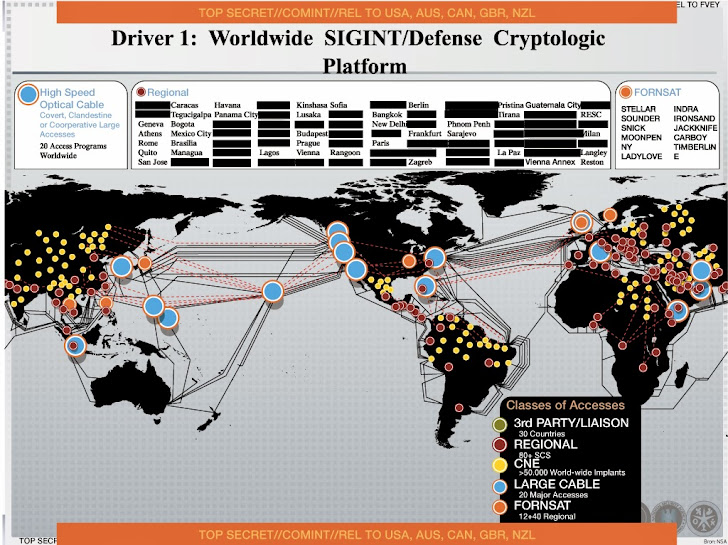
A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect

A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect

Michael J Myers Emerging Roles Of Combat Communication Squadrons In Cyber Warfare As Related To Computer Network Attack Defense And Exploitation by Michael J Myers | Willowbrook Shopping Centre

National Security Agency on LinkedIn: #computerscience #computerscientists #digitalnetworks | 17 comments

The Exploitation of Instant Messaging to Monitor Computer Networks Using XMPP: A Study Focuses on School Computer Labs | Semantic Scholar

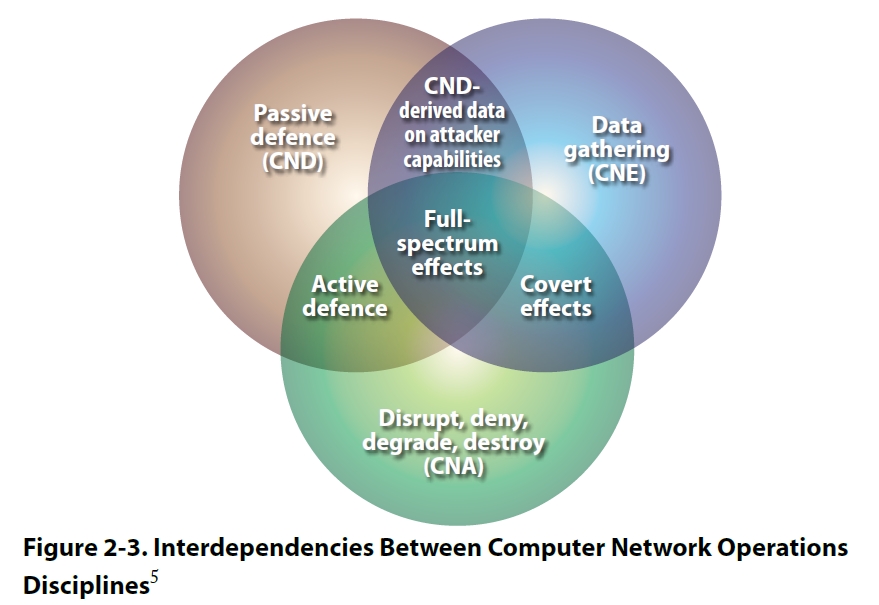

/cloudfront-ap-southeast-2.images.arcpublishing.com/nzme/KTYPA66EVVGTLICWV2IJP2OS4U.jpg)